3. A detailed look at the security of Priva services
Priva services - and the infrastructure behind them - can be divided into multiple security layers. It starts with the control system. The control system connects to the Cloud through the Edge Gateway. In the Cloud the data is stored and the services are hosted. This is also where users access their services. See the picture below for the service architecture overview. The security of each of these components within the service architecture is discussed next.
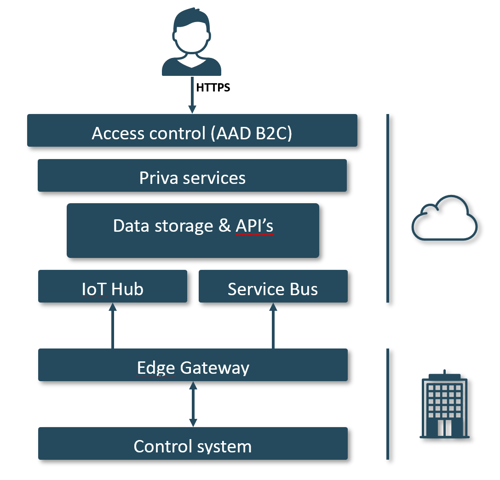
3.1 The control system
The control system is the network of controllers that controls the climate installation. Generally, controllers and other related devices have limited security. The network traffic between control system components is often also unencrypted due to the use of unencrypted protocols and the need for interconnectivity. Those devices are expected to function 24/7 for more than a decade and, as such, are incredibly hard to keep up to date and secure during their entire lifespan.
Control systems should always use a dedicated technical network that provides security separating the control system from any possible means of outside access. Therefore control systems should never run on networks with internet access.
3.2. The Edge gateway
In order to use Cloud services, the control system has to connect to the internet. So we use the Priva Edge Gateway to provide a secure interface between the control system and the internet. The Priva Edge Gateway is a closed system that can only be configured and used for Priva services. Non-Priva software cannot be run on it.
It uses three separate network cards that cannot be bridged to physically separate the internet from the technical network that our controllers use. This keeps the controllers logically separated from the internet.
The first network card, LAN1, is for connection to the outside world. To protect against potential intruders, it uses outbound connections and only uses the minimally necessary inbound connections. Any communication between the control system and the Cloud is always initiated by the Edge Gateway.
LAN2 is for connecting the Edge Gateway to the technical network. To connect with the other devices, LAN2 has ports open to inbound traffic.
LAN3 is for on-site service. On LAN3 the Local web UI can be accessed through which device and network settings can be accessed and changed.
We use standard Microsoft components to communicate between the control system and the Cloud. Specifically, our services use Microsoft Azure’s IoT Hub and Service Bus. The network traffic between the Priva Edge Gateway and the Cloud is encrypted. In contrast to some other methods of accessing such as VPN, our architecture uses a message-based system, so there is no full data link between the control system and the outside world. Only very limited relevant data is exchanged.
3.3. Security of the Cloud; access control
The primary defense against unauthorized user access to our Cloud services is an authentication layer based on the OAuth2 protocol. We use Azure Active Directory B2C (AAD B2C) as our identity provider and an Identity Server implementation that provides the authorization rules for these identities. We enforce that communication with all our services is done via HTTPS (TLS v1.2 or higher).
After a user authenticates with AAD B2C its permissions are encoded in a JSON Web Token and signed using a private key. Whenever one of our applications wants to access your data, it must present the token to the service that stores it. The service will then check if the token was not tampered with, using a public key and if the user has permission to access the requested resource.
Users of Priva services use Access Control, which enables administrative users of an organization to control which accounts have access to which features and locations. At the point of sale, we give access rights to the buyer of the service, after which they can invite others and control their rights.
By default, MFA (Multi-Factor Authentication) is enabled for new users providing increased security during the login process. In addition to the user’s password, MFA uses a second authentication factor like a text message with a one-time code to get access to the Cloud services.
In addition, our services also support the use of the customer AAD, with which the customer can have more extensive control over the security policies.
3.4. What endpoints do Priva services use?
To connect to the services in the Cloud, our Edge Gateway uses Fully Qualified Domain Names (FQDNs). The full overview of specific FQDNs is available in the Edge Gateway documentation.
3.5 Who owns the data?
Our policy is that the data belongs to whoever owns the system that generates it. We do however retain the right to use this data for development purposes after it has been made anonymous. Priva’s full policy regarding the use of data is described in our general and service specific Terms & Conditions and our Privacy Policy.
3.6 Where is your data stored?
All our Cloud services are hosted in Microsoft Azure’s West Europe region. The datacenters in this region are currently physically located in/near Amsterdam, the Netherlands. For disaster recovery purposes however, these Microsoft datacenters are paired with those in Azure’s North Europe region which are physically located in/near Dublin, Ireland. In emergency situations, your data might be transferred between these two datacenter locations. These data transfers always use Microsoft’s privately-owned communication infrastructure.















